|
1 | | -When a suspicious email is detected, you can use this pack to determine whether the email is part of a bigger phishing campaign, and to understand its scale and potential risks. |
2 | | - |
3 | | -## What does this pack do? |
4 | | - |
5 | | -The pack includes the **FindEmailCampaign** script which enables you to: |
6 | | -- Filter past email incidents according to multiple search criteria such as incident types, email body and/or subject, email sender and more. |
7 | | -- Define criteria for a collection of related email incidents to be considered a campaign: minimum number of incidents, minimum number of unique recipients and machine-learning driven similarity threshold between emails. |
8 | | - |
9 | | -The script output indicates whether a campaign was identified. When a campaign is identified, more information about the campaign is provided: number of incidents involved in the campaign, indicators involved in the campaign and more. |
10 | | -This allows the user to take additional steps on the campaign findings, like blocking the email of the campaign sender or notifying the email recipients about the campaign. |
11 | | - |
12 | | - |
13 | | -## How does this pack work? |
14 | | - |
15 | | -- You can use the FindEmailCampaign script from this pack on any existing email incident to search through past incidents of the same type and identify campaigns. |
16 | | -- You can use the data gathered from the FindEmailCampaign script to close existing incidents as duplicates and to let the recipients know about the detected campaign. |
17 | | -- You can use the data gathered from the FindEmailCampaign script to identify malicious indicators used in the campaign and block them. |
18 | | -- The pack expects you to have pre-existing email incidents created from a mail listener such as EWS v2. |
19 | | -- The Phishing content pack is required because the **FindEmailCampaign** script uses the **FindDuplicateEmailIncidents** script from that pack. |
20 | | - |
21 | | -_For more information, visit our [Cortex XSOAR Developer Docs](https://xsoar.pan.dev/docs/reference/packs/phishing-campaign)._ |
22 | | - |
23 | | -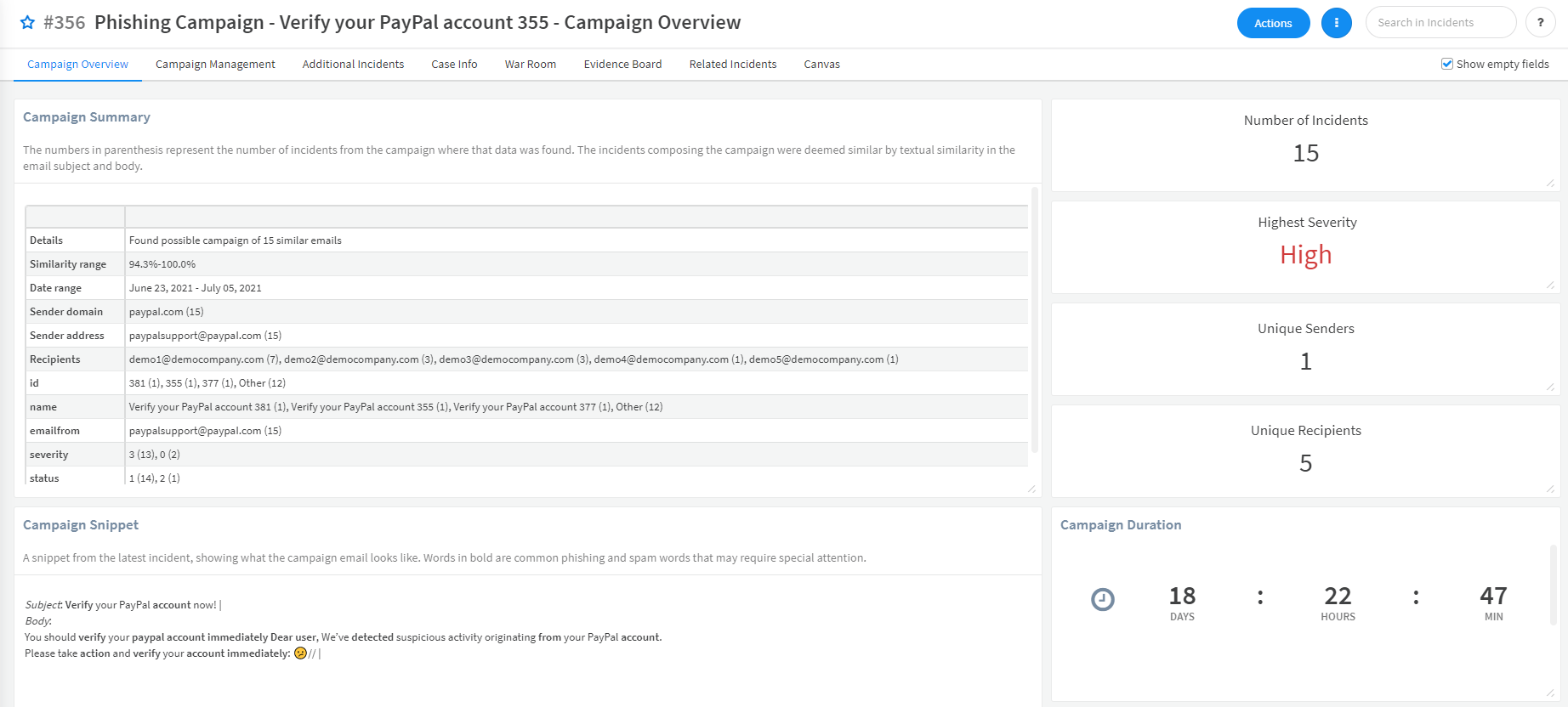 |
24 | | - |
25 | | -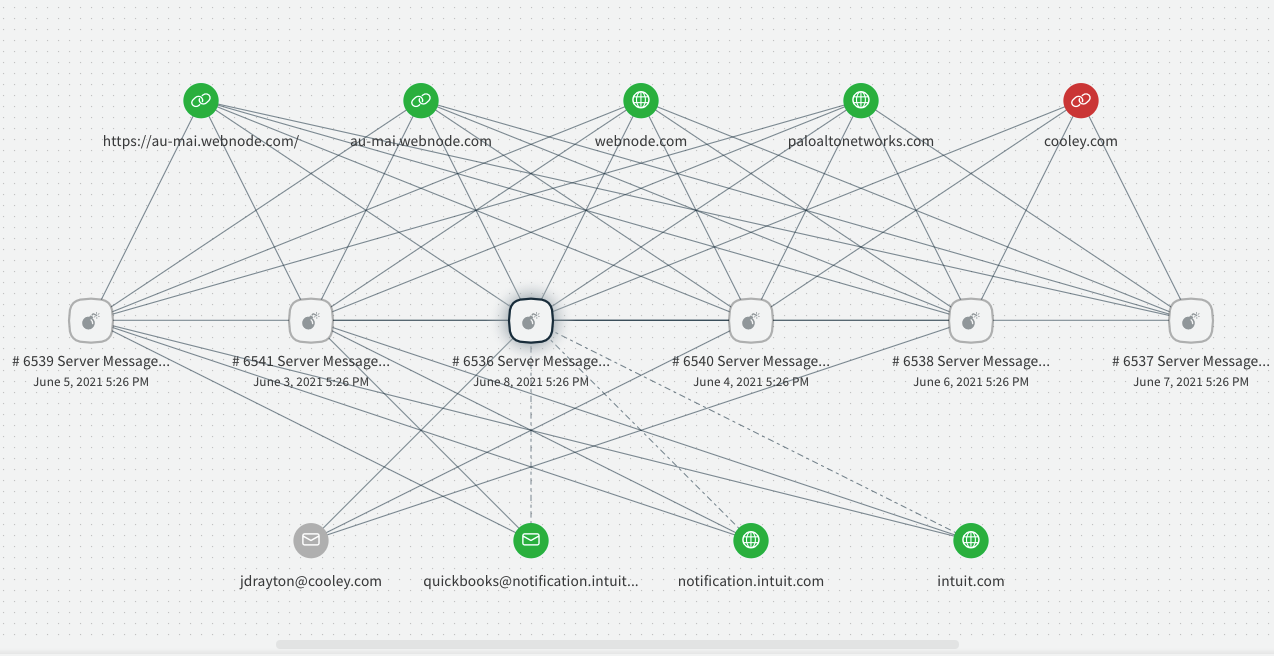 |
26 | | - |
27 | | - |
28 | | - |
| 1 | +When a suspicious email is detected, you can use this pack to determine whether the email is part of a bigger phishing campaign, and to understand its scale and potential risks. |
| 2 | + |
| 3 | +## What does this pack do? |
| 4 | + |
| 5 | +The pack includes the **FindEmailCampaign** script which enables you to: |
| 6 | +- Filter past email incidents according to multiple search criteria such as incident types, email body and/or subject, email sender and more. |
| 7 | +- Define criteria for a collection of related email incidents to be considered a campaign: minimum number of incidents, minimum number of unique recipients and machine-learning driven similarity threshold between emails. |
| 8 | + |
| 9 | +The script output indicates whether a campaign was identified. When a campaign is identified, more information about the campaign is provided: number of incidents involved in the campaign, indicators involved in the campaign and more. |
| 10 | +This allows the user to take additional steps on the campaign findings, like blocking the email of the campaign sender or notifying the email recipients about the campaign. |
| 11 | + |
| 12 | + |
| 13 | +## How does this pack work? |
| 14 | + |
| 15 | +- You can use the FindEmailCampaign script from this pack on any existing email incident to search through past incidents of the same type and identify campaigns. |
| 16 | +- You can use the data gathered from the FindEmailCampaign script to close existing incidents as duplicates and to let the recipients know about the detected campaign. |
| 17 | +- You can use the data gathered from the FindEmailCampaign script to identify malicious indicators used in the campaign and block them. |
| 18 | +- The pack expects you to have pre-existing email incidents created from a mail listener such as EWS v2. |
| 19 | +- The Phishing content pack is required because the **FindEmailCampaign** script uses the **FindDuplicateEmailIncidents** script from that pack. |
| 20 | + |
| 21 | +_For more information, visit our [Cortex XSOAR Developer Docs](https://xsoar.pan.dev/docs/reference/packs/phishing-campaign)._ |
| 22 | + |
| 23 | + |
| 24 | + |
| 25 | + |
| 26 | + |
| 27 | + |
| 28 | + |
0 commit comments