-
Notifications
You must be signed in to change notification settings - Fork 6k
Multipartfile request with no authentication is still consumed even after an AccessDeniedException is thrown #7060
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Comments
|
Thanks for the report @a-sayyed! I'm not sure this can be avoided all together. This is a common issue for multipart requests. For example, CSRF needs to process the parameters to determine if the request is valid. So I can better understand your issue, can you please explain what specific problem this is causing you? I understand a file can be uploaded, but this doesn't seem any more of a problem than a user can make requests to the server (the difference is the file is written to disk vs just being in memory). |
|
Thank you for the explanation @rwinch! |
|
It isn't possible when security needs to read anything from the body (i.e. CSRF parameter, form body, etc). While I understand this reduces the risk, it seems that if you are in trouble for a DoS attack, you still have this problem if the user is authorized to make the request (many attacks are user's with permissions). If we modify the request to ignore saving the parameters, then a user that has the session time out while filling out a multipart form is likely to run into an issue where a page requires certain parameters and the saved request no longer has them which would result in surprising errors. Instead, I'd suggest that we modify the configured HttpSessionRequestCache.requestMatcher to ignore multipart requests. Would you be interested in submitting a PR for it? In the meantime, you can explicitly create and configure a |
|
Hi @rwinch sounds good!, I will let you know once I am done 👍 |
Summary
As explained by @wilkinsona in this related issue: spring-projects/spring-boot#17345, a multipartfile request with no authentication to a secure endpoint, results in an
AccessDeniedException(when theHiddenHttpMethodFilteris disabled). This is handled inExceptionTranslationFilter.handleSpringSecurityException(HttpServletRequest, HttpServletResponse, FilterChain, RuntimeException)which results in the creation of aDefaultSavedRequest. This callsjavax.servlet.ServletRequest.getParameterMap()which causes the multipart request to be consumed and parsed.Actual Behavior
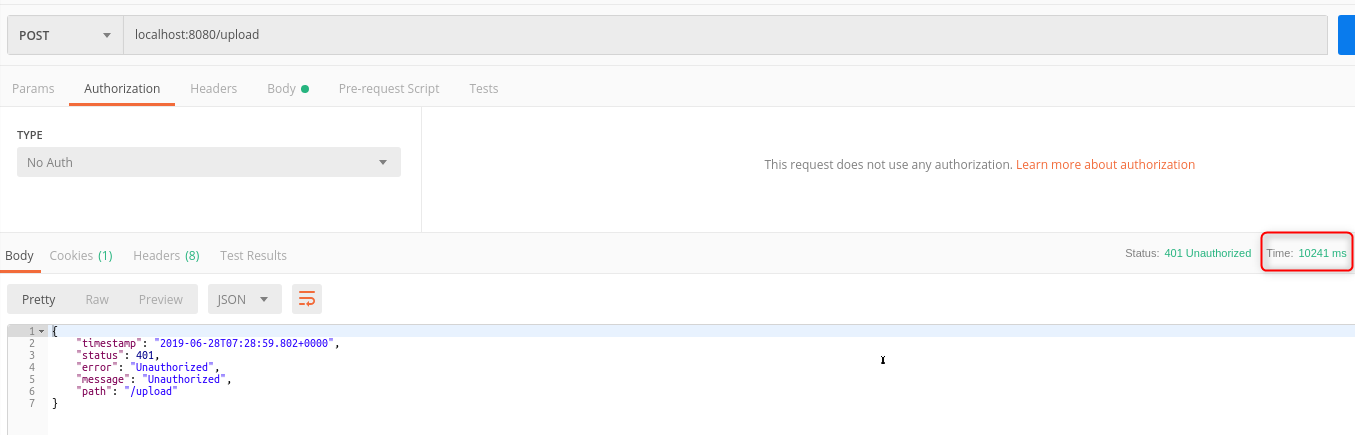
Multipart file request with no Authentication to a secure endpoint results in the request being parsed and consumed anyway, then the client gets a
401 UnauthorizedExpected Behavior
Multipart file request with no Authentication to a secure endpoint should result in the request not being parsed or consumed, and the client gets a
401 Unauthorizedas soon as anAccessDeniedExceptionis thrown.Configuration
Please see the attached sample. You will need to add the property
spring.mvc.hiddenmethod.filter.enabled=falseto theapplication.propertiesfileVersion
2.1.6.RELEASE
Sample
https://github.com/a-sayyed/spring-jetty-secure-multipartfile-upload-bug
The text was updated successfully, but these errors were encountered: