-
Notifications
You must be signed in to change notification settings - Fork 3
state machine impl #8
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
and first iteration of a server
|
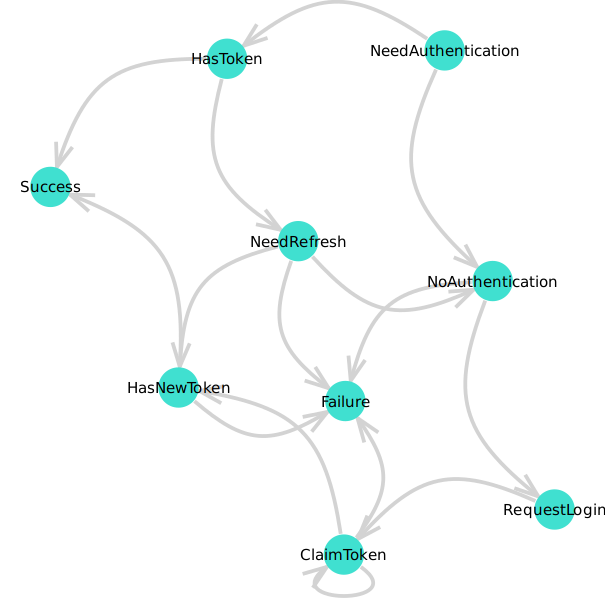
Looks like a great improvement in clarity on first glance. Might be useful to document the state machine in a diagram. |
|
That's the plan. I was kinda hoping to automate that though :) |
|
Would also be great to put type annotations on various fields where possible. |
|
There's also the question whether we care about Julia versions older than 1.3 here. I can just switch to Downloads.jl if not. |
|
We are encountering following error https://gist.github.com/bmharsha/590067fb52899d520146bd8ea3e08001#file-error1-md when we tried using PkgAuthentication.jl from this PR. Pkg server was set to |
|
I made some tweaks to this and asked some questions in a PR to this PR: #9. Let's address the questions (marked with "QUESTION") and then we can figure out whether to merge my changes or not. I'm especially interested in the expiration logic. Is the key ever |
|
Left a review over at #9 that should address your questions. Adding another |
some tweaks and questions
|
Alright, pushed a commit that addressed your concerns and improved the |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Looks great to me aside from the one question about @debug versus @warn.
and first iteration of a server