Description
Published Research
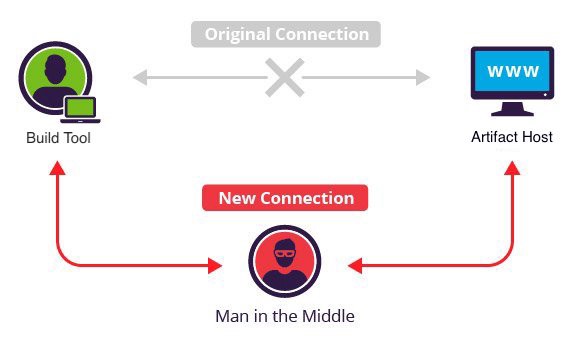
Want to take over the Java ecosystem? All you need is a MITM!
CVE ID(s)
- CVE-2019-11404
- CVE-2019-10248
- CVE-2019-10249
- CVE-2019-10240
- CVE-2019-10249
- CVE-2019-12728
- CVE-2019-10102
- CVE-2019-11405
There are other projects without CVE numbers that need assignment still:
https://docs.google.com/spreadsheets/d/1zemxj8QdIp0saqvwJx6Po1KnyEmJXl2KC_0j0SLd_2E/edit#gid=0
Report
CWE-829: Inclusion of Functionality from Untrusted Control Sphere
CWE-494: Download of Code Without Integrity Check
At the beginning of 2019, I began a multi-month long research project into the use of HTTP instead of HTTPS across the Java ecosystem. I found that many of the most popular projects in the ecosystem were using HTTP to resolve and upload artifacts that those projects downloaded and built.
This included projects such as these:
- Kotlin Compiler
- Groovy Compiler
- Jenkins
- Many JetBrains projects
- Many Apache projects
- Many Eclipse projects
- Gradle building itself
As part of this research, I reached out to many of the most popular artifact servers in the Java ecosystem and asked them to join an initiative to formally decommission the use of HTTP on January 15th, 2020.
- Sonatype Maven Central
- JFrog JCenter
- Gradle
- Spring
The links to the announcements by these organizations can be found here.
At the time, the team at Sonatype Maven Central let me know that after analyzing their traffic for a month, they determined that 25% of their downloads still used HTTP instead of HTTPS.
- Are you planning to discuss this vulnerability submission publicly? (Blog Post, social networks, etc). We would love to have you spread the word about the good work you are doing
I already have, but would post an updated post after this was merged.
Query
Unfortunately, since QL doesn't allow me to create querries against Gradle build logic yet, I'm only currently able to support Maven Pom XML files. However, this should still cover ~50% of the entire Java build tool ecosystem.